The past year saw an increasing number of cyber-attacks, with mainstream media covering stories of widespread targeted attacks on the ŌĆ£software and application layerŌĆØ causing irrecoverable damage to the brand and reputation of companies and critical Information Infrastructures of Nations.
Cyber war fare is now a strategic lever strongly considered by nation states to shock enemy nations without firing a single shot or a drop of blood spilled, an entire country can be crippled by a well-coordinated cyber-attack;
While software applications are the engine of innovation they are today the biggest attack vector with more than 85 % of the attacks targeting the application layer, Having the potential to devastate companies and Nations.
Thus the traditional approach of building security counter measures around the Infrastructure and network layer in isolation donŌĆÖt work anymore as attacks on applications are continuing unabated. Hence there is a paradigm shift in idea to apply an application and data centric security strategy as opposed to the traditional approach.
An application-centric approach shifts the security focus from the tools and processes, to the business and services they are designed to enable, thus ensure that security serves the strategic needs of the business.
Data and Applications are the oil that lubricates institutions, organizations, governments and smart cities. Data is the crown jewels that need to be secured on high priority. Organization and governments gather process and distribute data in real time with the aim of increasing efficiency and improving situational awareness. This data is priceless. Cyber Criminals and state sponsored Cyber espionage actors are in pursuit of this data – the crown jewels; if stolen can cripple companies and governments.
Hence application security should be amongst the highest priority
The number of security incidents that have been handled by Indian Computer Emergency Response Team (CERT-In) over the last few years has increased exponentially. If we compare the security incidents of 2014 with 2013, there has been a marked increase of 82%. Recent research shows 85 % of these attacks are targeting the application layer.

Attacks on applications are among the costliest incidents organizations can face. One coordinated attack reportedly stole US$1 billion from 50 different companies. Also there is a steep 135 % increase in financial loss reported this year compared to the previous yearŌĆÖs trend of 20-30% over the years before. Not only has the number of incidents increased, but the average loss resulting from an incident borne by an Indian organization has also increased by close to 8%.
A major concern reported by security research analyst is that the newly hyped smart cities are implementing newer technologies at a very fast pace without testing and performing application security assessment. As a result of this, it is predicted that an unprecedented cyber-attacks will surface in smart cities infrastructure. In addition to financial and reputational impact there can be threat to human life due to disruption of Critical infrastructure like power systems, water supply and transportation networks.
The threat to applications are real and its Vital to orient security strategies to protect application and data by securing the software code and instituting security processes across the software development, deployment, maintenance life cycle and establishing multi layered security counter measures throughout the infrastructure value chain that protects the application.
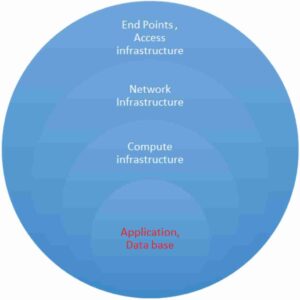
Picture of Layered Security to protect the crown Jewels the application
When an organization takes an application centric approach to security, there is an automatic shift of aligning the security to business risks and a paradigm shift from the traditional piece meal point solution approach to a more comprehensive strategic dimension. The key aspect of the Application Centric Security Strategy is to break the security silos and establish an integrated 360-degree view of the security processes and solutions across the infrastructure value chain aligned to protect the crown jewels which are the applications and data.
BizCarta Technologies is a pure play Information risk management consulting services company, providing high quality cyber security consulting services to SMBs and large corporate helping companies establish a robust cyber security strategy and a road map to deal with the evolving threats in a systematic manner.
Serving customers from diverse sectors such as IT, ITES, Ministry of Defense, leading Gartner rated software development including leading global banking software application developing firm and manufacturing industries, BizCarta has helped companies in predict, detect, mitigate and sustain from cyber threats by building secure foundation pillars for risk reduction to acceptable level. We are passionate about what we do and we do it with the best of our abilities to meet the business needs, secure the infrastructure, support the business growth strategy, empower board members through sustainable results and roadmap.
Director Cyber Security and Solution Design ŌĆō Roy Ramkrishna says ŌĆ£Our mission is to support organizations in building a resilient cyber defense platformŌĆØ. ┬ĀThe critical tenets of which are
The best defense is to learn from offense┬ĀŌĆō Use knowledge of actual attacks that have compromised systems and use these events to build effective, practical defenses. Classify the attacker maturity level and perform red teaming exercise on infrastructure to find the 5 WŌĆÖs – why, who, what, where, and when of the attack vectors. Physical Security is also playing an important role. Most of the insider threats are due to lack of proper physical access control.
Prioritize the priority┬ĀŌĆō Ask the question is compliance your priority or true risk reduction? Invest first in appropriate controls that will provide greatest risk reduction of the application layer and critical infra. Availability against most dangerous attacks.
Governance and Metrics┬ĀŌĆō Define operational governance and strategic governance through a mutual metrics to provide a common language amongst CXO, auditor, IT specialist and operational security team.
Continuous Improvement Culture ŌĆō┬ĀPerform regular assessment to test and validate the effectiveness of the current state of security measures and provide inputs to drive the priority. Conduct frequent User awareness exercise and arrange role based information security training programs.
Automation ŌĆō┬ĀManual process had to be automated to improve defenses through speed of aggregation, detection, mitigation and continuous measurement from defined metrics.┬Ā Invest in right skills and enforce a culture of knowledge sharing.
BizCarta team is a unique combination of business and core security engineering experts who plan market domination in the morning, wrack our brains over chess at noon, and hunt the hackers at night ŌĆō enjoying every moment.
With expansion in customer base and timely project execution, the company has received attention as a promising Information risk management consulting firm. Presently operating from India and USA, BizCarta has extended its operations to EMEA Region.
By proficiently working on its consulting framework Bizcarta envisions becoming one of the top 10 Information Risk Management Cyber Security Consulting & Services companies in India by the year 2020.
AN APPLICATION CENTRIC CYBER SECURITY STRATEGY NEEDED TO SURVIVE THE ONSLAUGHT


